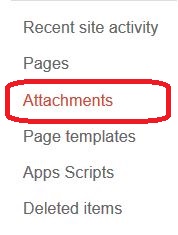
Upload file to Google sites: Attachments guideline
Google sites is the best place to create your website for free. Here you can create or use the existing web templates too. To upload the files such as audio, text, Image or any other files you need to manage your site to upload the attachments to Google sites. Lets move to the Google Sites. … Read more