Steganography techniques can be used to hide confidential data. Lets us see the alternate data stream method to hide the confidential files inside another file and that secret file remain undetected unless close inspection. ADS method added to the NTFS to support Macintosh Hierarchical file system. It uses the resource fork to store information for a file.
Alternate data stream method uses colon(:) operator to hide files.
Hiding Secret message Inside Text File: Open up the command prompt inside windows system and start following the steps:
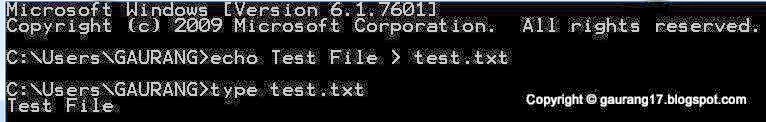
Create Echo test file and view it using Type command.
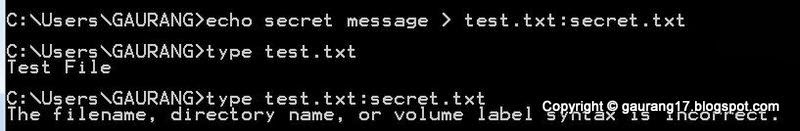
Create Secret message and bind it with the test.txt using colon(:) and view it by type command.
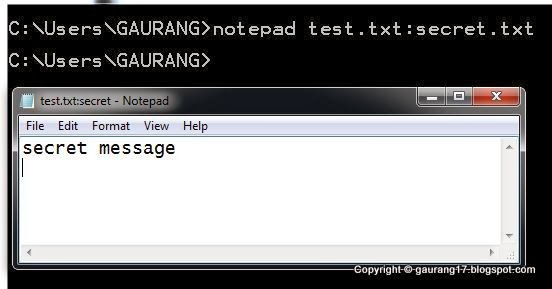
View Secret message by Using notepad as below.
Hiding Executable inside text File:
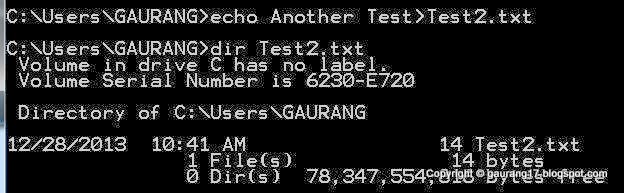
Create Echo test file and you can view it by dir command.
Create Echo test file and you can view it by dir command.
Copy calc.exe file from system folder to the local or you can access it directly by giving the path. Here we have used Calculator to hide, you can choose any exe you want.
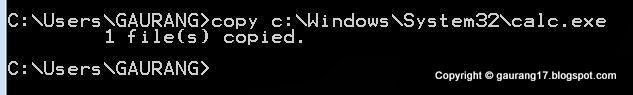
Bind the Calc.exe with Test2.txt and name it with another exe to hide.
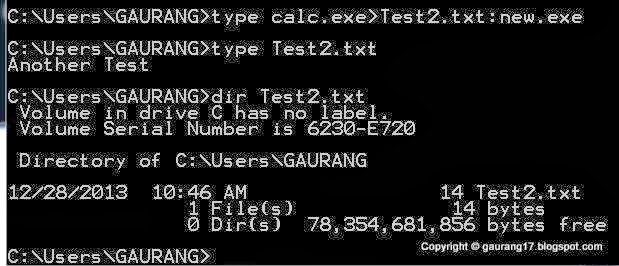
Run the Hidden EXE file by giving the Alternate path by colon(:) with start command.
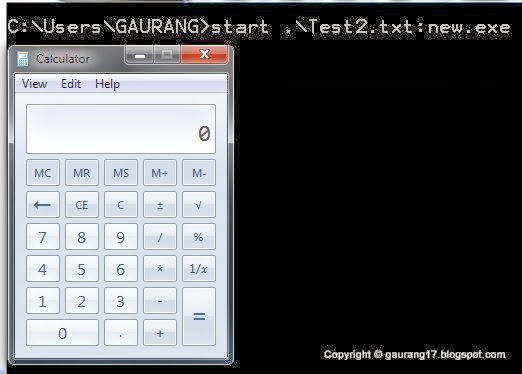
This will be helpful if you want to share some private data on the network because the file looks like the normal file but it actually contains the hidden secret message or executable. So using ADS you can hide the confidential data.
Using LADS- (List Alternate Data Stream) you can view the file which are processed through ADS. Type lads c:\ to view the ADS files inside the C: drive. So LADS used to detect the ADS.
Comment if you have any queries.
